Social media-based terrorist communication and the issues of large-scale fake news and hate speech has evoked national security concerns for the government. Concerns of persisting child sexual abuse material (CSAM) proliferation has also been prominent. Recognizing the role of social media in such a context, the government has pushed for transparency and a crackdown on such content. In the same line of interventions, the government has pushed for tech companies to “not use encryption as an excuse to hold up investigations”.
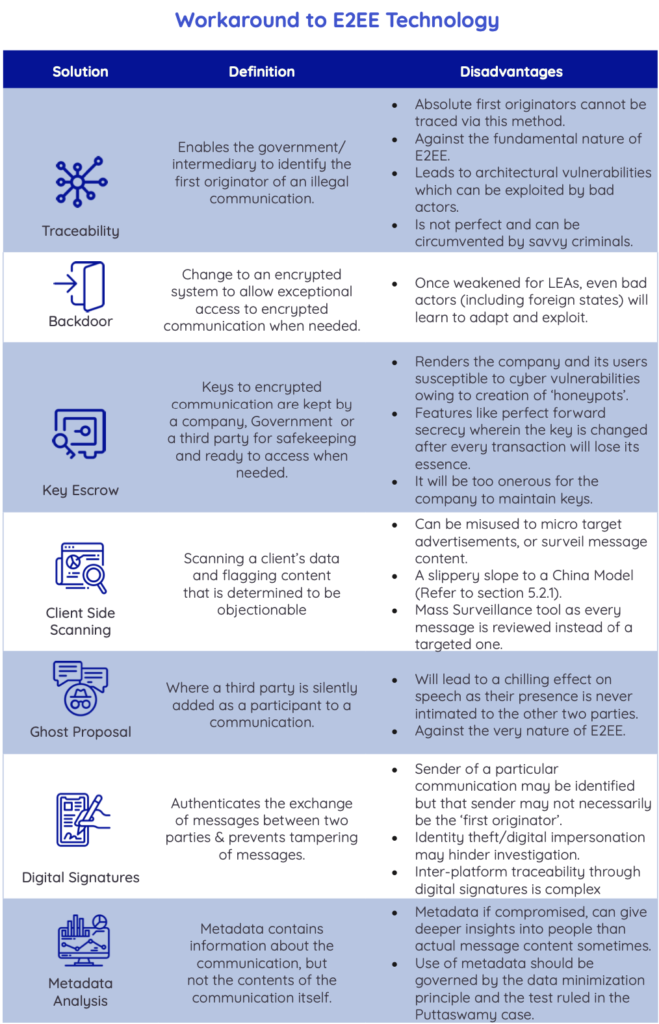
While the concerns pertaining to national security, CSAM, and fake news are all legitimate, enforcing traceability is not a viable remedy. The traceability mandate envisaged in the IT Rules, 2021 has a significant impact on user privacy, integrity, and confidentiality of information. Any move towards enforcing traceability renders India’s population vulnerable to erosion of anonymity and restriction of free speech. Writ petitions against the traceability mandate have been filed before Kerala, the Madras, and the Delhi High Courts. There is a need for a robust encryption regime in India. The quest to make platforms more accountable must not put millions of users at risk.
Why Tracing Messages is a Challenge
Exactly a year ago, the Indian government notified the “Information Technology (Intermediary Guidelines and Digital Media Ethics Code) Rules, 2021”, under the Information Technology Act, 2000. Many of the provisions of the IT Rules have been debated and discussed in the context of forced censorship and a paradigm shift in regulating digital and social media. However, these regulations formally put to paper the long-held demand of the government for messaging platforms to be more accountable- with the mandate on enabling identification of the person who first sent a message on the platform. Platforms that have committed to user privacy are facing pushback from government mandates.
The demand of the government to trace the first originator entails identifying the person who first sent the illegal content on a platform. This is a significant blow to the encryption regime and the technological convergence towards greater user privacy.
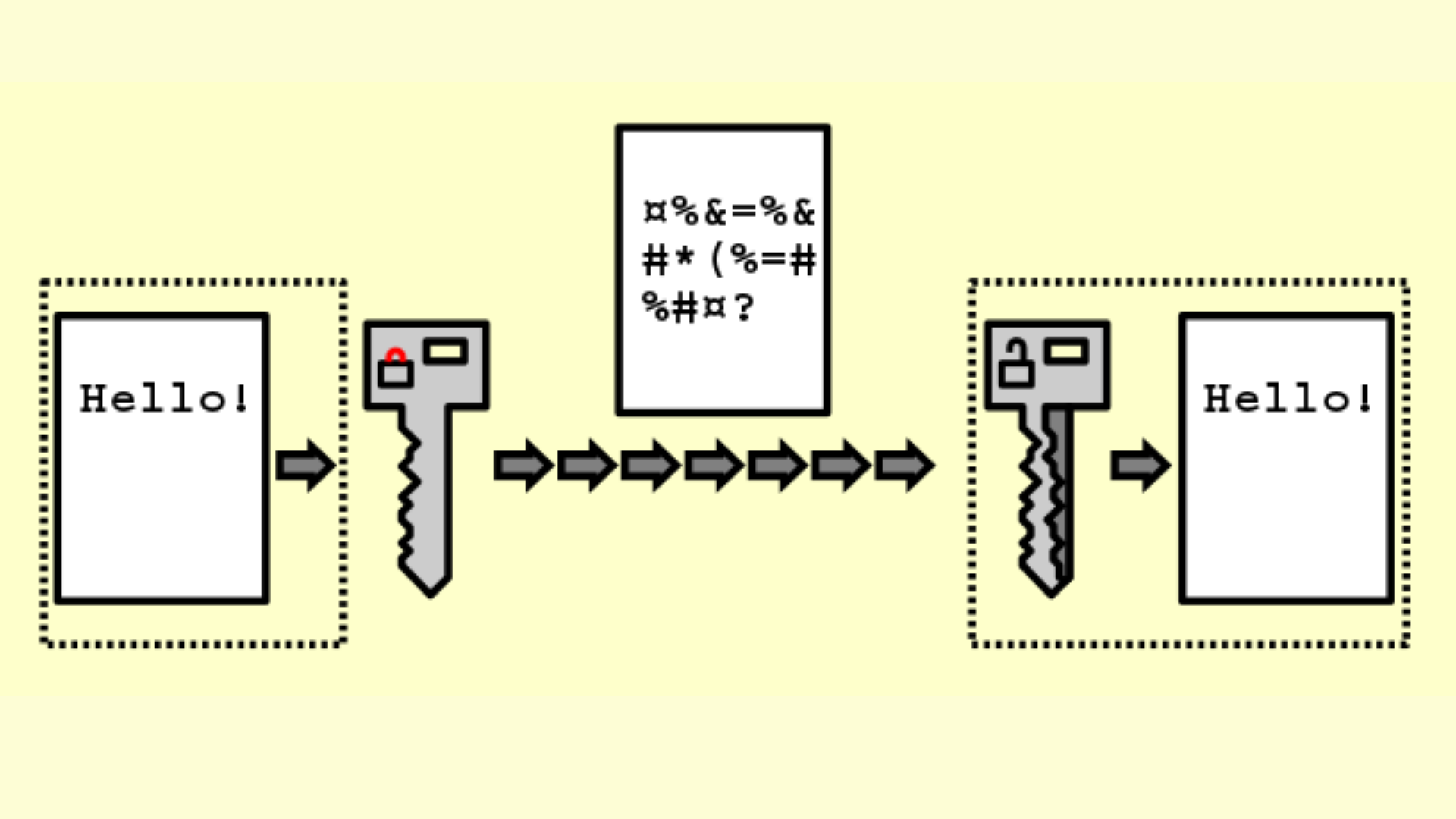
Despite explicitly maintaining that it does not seek to break end-to-end encryption, the demands of the government are incompatible with the architecture of the end-to-end encrypted (E2EE) platforms. These platforms encrypt personal communications end-to-end between the sender and the recipient, and no third party (not even the service provider) has access to the communication. Two prominent methods- digital signatures (Kamakoti Proposals) and Hashing, have been touted as less intrusive methods to allow traceability but are replete with challenges.
The proposal of digital signatures was put forth by Professor V Kamakoti of IIT Madras and requires attaching metadata tags identifying the sender of the message to the message. Accordingly, every message you send will also have your name, depriving you of your privacy. Moreover, even if someone else forwards your message, it will still have your name- even if you didn’t mean it to be shared further. It is also technologically possible to spoof this arrangement and skip the metadata tags, so the savvy criminals will still be able to hide and only the law-abiding citizens will face the brunt of this mandate.
The latest traceability proposal expects a company like Signal or WhatsApp to store the hash value of each message sent on their platform. A hash value is a one-way conversion of content data into a unique alphanumeric code. Unlike encryption, after hashing the hash value cannot be converted back to the original content.

In other words, the companies are expected to store a fingerprint of all the messages sent by every citizen. Hacking or abuse of this humongous database of messages sent by Indians is a cybersecurity nightmare. It is also pertinent to note that both these methods are only enforceable for Indian clients identified via the +91 phone number. A savvy criminal can simply buy a foreign phone number for $1 or simply pay a person who does not understand the consequences, to be the first originator. All these efforts render the entire citizenry vulnerable only to catch a low-hanging fruit, while the savvy criminals hatching conspiracies simply shift to unregulated encrypted apps or create their own encrypted apps.
The hashing method proposed by the IT Rules, 2021 has much more severe ramifications of falsely implicating innocent users while savvy criminals can side-step any scans by changing the hash value of the offending messages. The Dialogue’s Technical Brief based on a workshop led by Dr. Sandeep Shukla, Professor of Computer Science and Engineering, IIT Kanpur and Mr. Anand Venkatnarayanan, Strategic Advisor, DeepStrat, delves into the challenges posed by these alternatives.
Is Encryption Really Threatening National Security?
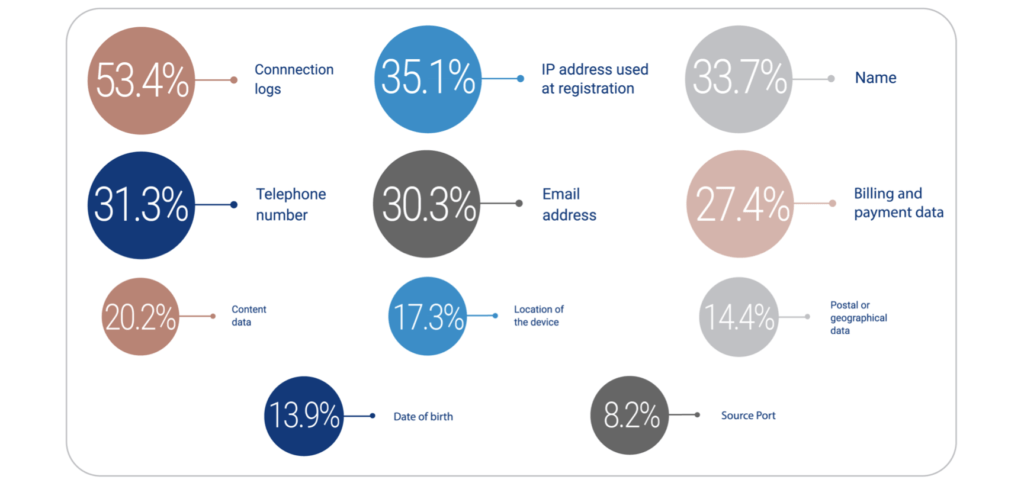
While governments across the world have cited national security as a concern to weaken encryption, none have demonstrated empirically if it is a real challenge. On the contrary, the SIRIUS EU Digital Evidence Report (2021) showed that only 20% of the 208 law enforcement officials interviewed selected ‘Content Data’ amongst the top 3 data sets required for investigation. For the remaining 80%, the following metadata was what they needed. This empirically establishes that we do not need to weaken encryption to fulfil legitimate state objectives and access to metadata is enough.
Closer home, The Dialogue and DeepStrat conducted a study on the National Security Implications of Weakening Encryption based on qualitative inputs from veterans in law enforcement, intelligence agencies, the military & India’s tech community as well as a deep study of global legal and technical standards. The report identified that the key challenge to nabbing criminals in cyberspace is not encryption, but the inability to utilise even metadata owing to concerns like access to technology and lack of workforce skilled at analysing metadata.
The report draws a parallel between military power and cyber power. A net importer of weapons with no indigenous capability to build, maintain and service them, a country cannot be a credible military power. On the same tangent, a net importer of encryption technologies with no capability to build, break and maintain them, cannot be a credible cyber power. Given that more and more weapon systems and critical infrastructure are getting digitised, a nation-state that has encryption debt (like India) will always be vulnerable.
Like how a country in debt cannot hope to come out of it by going deeper into debt, encryption debt cannot be reduced by becoming more hostile to encryption as it erodes whatever cyber capabilities that exist, across the spectrum. Accordingly, an action plan for reducing encryption debt is a must.

Law Enforcement and Metadata
The success of Project Trojan Shield, wherein over 500 criminals were arrested, explains how ingenious use of encryption tech can be utilised to catch criminals. Herein the police planted a compromised encrypted App ‘An0m’ in a criminal network to surveil only the bad actors. The project relied on traditional surveillance manoeuvres to target defined actors, instead of surveilling everyone.
Explaining the importance of reassessing the policy debate around encryption Anand Venkatanarayanan, Strategic Advisor, DeepStrat and principal author of the study by The Dialogue and DeepStrat notes, “some amount of metadata in order for investigation will get you to the place where you can legally ask for more information without having to break end-to-end encryption”. The study accounts for the wide array of metadata available to the Indian law enforcement agencies, which would be crucial in catching criminals without putting the security of the citizens and the State at risk by weakening encryption.
Law Enforcement Authorities (LEAs) can access identification data like phone numbers, device identifiers, and IP address from service providers which when tied with an activity record of the target can reveal a lot. With the assistance of mobile manufacturers, a host of information like activation data, warranty status, device type can be accessed from the IMEI database. With data on IMEI number and IP Addresses, the LEAs can work to reconstruct the Wi-Fi networks that the target possibly connects to and the Internet Service Providers (ISPs) that serve the broadband connection. This will help identify the target’s location within a 50-metre range. The ISPs can also be requested to enable deep packet inspection revealing the list of applications that the target uses often which when analysed alongside activity records from the Central Monitoring System, messaging providers and online activity of the target on social media will help develop a detailed profile of the target. With so much that metadata can reveal, do we really need to weaken encryption?
We kill people based on metadata
━Former NSA Director Michael Hayden
Moving Forward: Assessing the Alternatives
There is a need to better appreciate the requirements of the law enforcement agencies. A nationwide study to gauge their modernisation and personnel requirement is a necessary first step in this regard. It is only after a clear understanding that where exactly the law enforcement agencies are facing challenges can meaningful solutions be offered.
In the meanwhile, tech companies and civil society should work with law enforcement agencies to build their metadata analysis capabilities. Any steps in this regard must be taken keeping in mind the data minimisation principle and align with the necessity, legality and proportionality test ruled in the Puttaswamy judgement.
The analysis so far points towards an important policy crossroads that India finds itself in: weakening encryption for more platform accountability but increasing user vulnerability, or risking prolonged conflict and continuing with the existing regime that upholds user privacy, anonymity, and integrity. A well-rounded choice in this regard would define the tone for a more conducive environment for encryption in India, and showcase its willingness to reduce technological gaps in a less confrontational manner.
Featured image credits: Johannes Landin.